Authentication Endpoints
Validate integration
Validate integration token and mark organization as integrated
GET
cURL
Why invoke the endpoint?
This enpoint allows partners to check if they have the right credentials and gives users an indication of successful integration.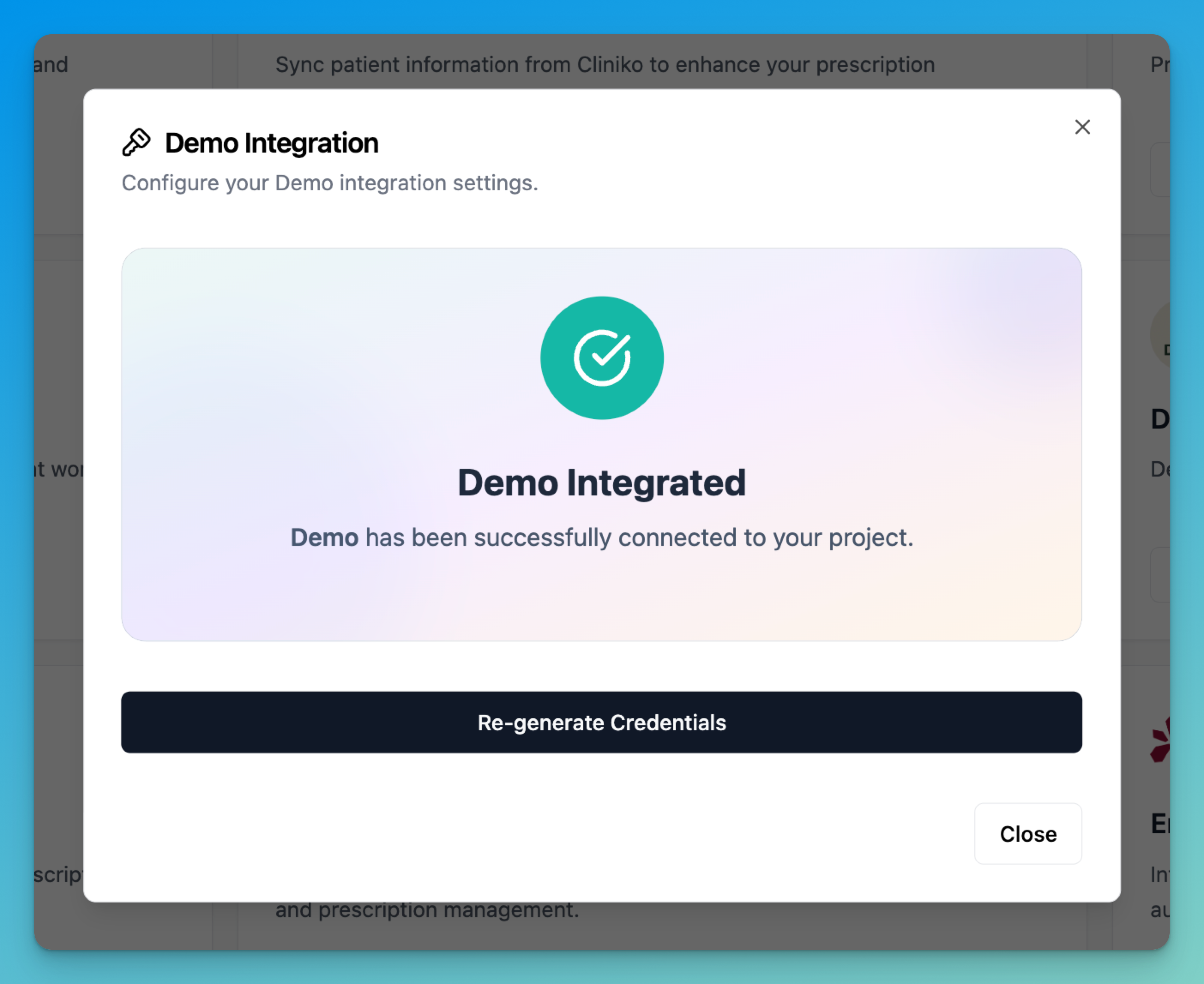
Response Examples
Success Response (200 OK)
Invalid Token (401 Unauthorized)
Missing Organization Secret (401 Unauthorized)
Validation Process
The endpoint performs an 8-step validation process:- Organization ID Validation - Verifies organization ID parameter is present
- Organization Secret Check - Validates x-organization-secret header presence
- Bearer Token Check - Ensures Authorization header contains valid Bearer token
- JWT Token Verification - Verifies token signature using RS256 algorithm
- Partner Credentials Lookup - Retrieves partner metadata from database
- Organization Secret Validation - Compares hashed organization secret
- Scope Validation - Ensures token has required CREATE_PATIENT scope
- Organization Ownership Check - Verifies user access to their organization
Required Headers
| Header | Required | Description |
|---|---|---|
Authorization | Yes | Bearer token with JWT authentication token |
x-organization-secret | Yes | Organization-specific secret for validation |
x-partner-secret | Deprecated | Use x-organization-secret instead |
Path Parameters
| Parameter | Type | Required | Description |
|---|---|---|---|
organization_id | string | Yes | Unique identifier for the organization |
Status Codes
| Code | Status | Description |
|---|---|---|
200 | OK | Token successfully validated and organization marked as integrated |
400 | Bad Request | Deprecated header used or invalid request format |
401 | Unauthorized | Invalid token, missing credentials, or insufficient permissions |
500 | Internal Server Error | Validation service failure |
Integration Side Effects
Upon successful validation, this endpoint automatically:- Marks Organization as Integrated: Updates the organization record with integrated PMS status
- Logs Integration Event: Records “New Partner Integration” metric for monitoring
- Enables Full API Access: Subsequent API requests will have full access to approved scopes
Error Handling
Recommended Implementation
Integration Notes
- One-Time Setup: This endpoint is typically called once during initial integration setup
- Token Requirements: Ensure your JWT token includes the
CREATE_PATIENTscope - Organization Secret: Use the organization-specific secret, not the deprecated partner secret
- Automatic Integration: Successful validation automatically enables your organization for API access
- Debugging: Always log the
requestIdfrom error responses for support requests - Token Expiry: Tokens are valid for 6 hours; validation will fail with expired tokens
Security Considerations
- JWT Verification: Tokens are verified using RS256 algorithm with rotating public keys
- Secret Hashing: Organization secrets are validated using HMAC-SHA256 with salt
- Scope Enforcement: Only tokens with appropriate scopes can validate successfully
- Organization Isolation: Users can only validate tokens for their own organizations
Authorizations
Bearer authentication header of the form Bearer <token>, where <token> is your auth token.
Headers
Organization secret for authentication - provided by Parchment
Path Parameters
Organization ID
Response
Token validation successful and organization marked as integrated
cURL

