Partner Token Creation
This guide explains how to generate authentication tokens for the Parchment API using the/v1/token endpoint.
Credentials Setup
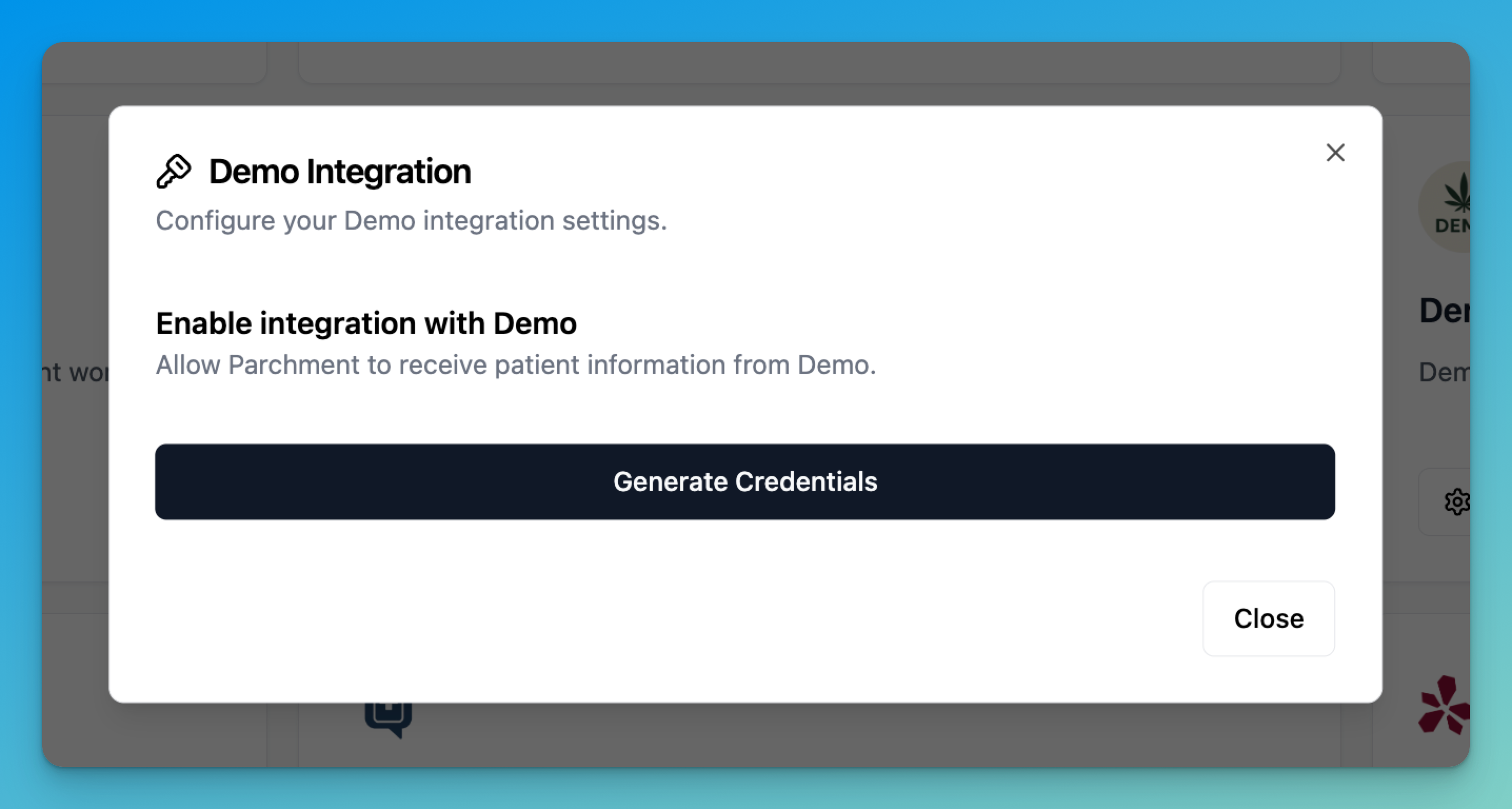
Before you can generate tokens, you need to obtain your partner credentials:- Navigate to Settings > Organisation > Edit > Partner Integrations in your sandbox environment
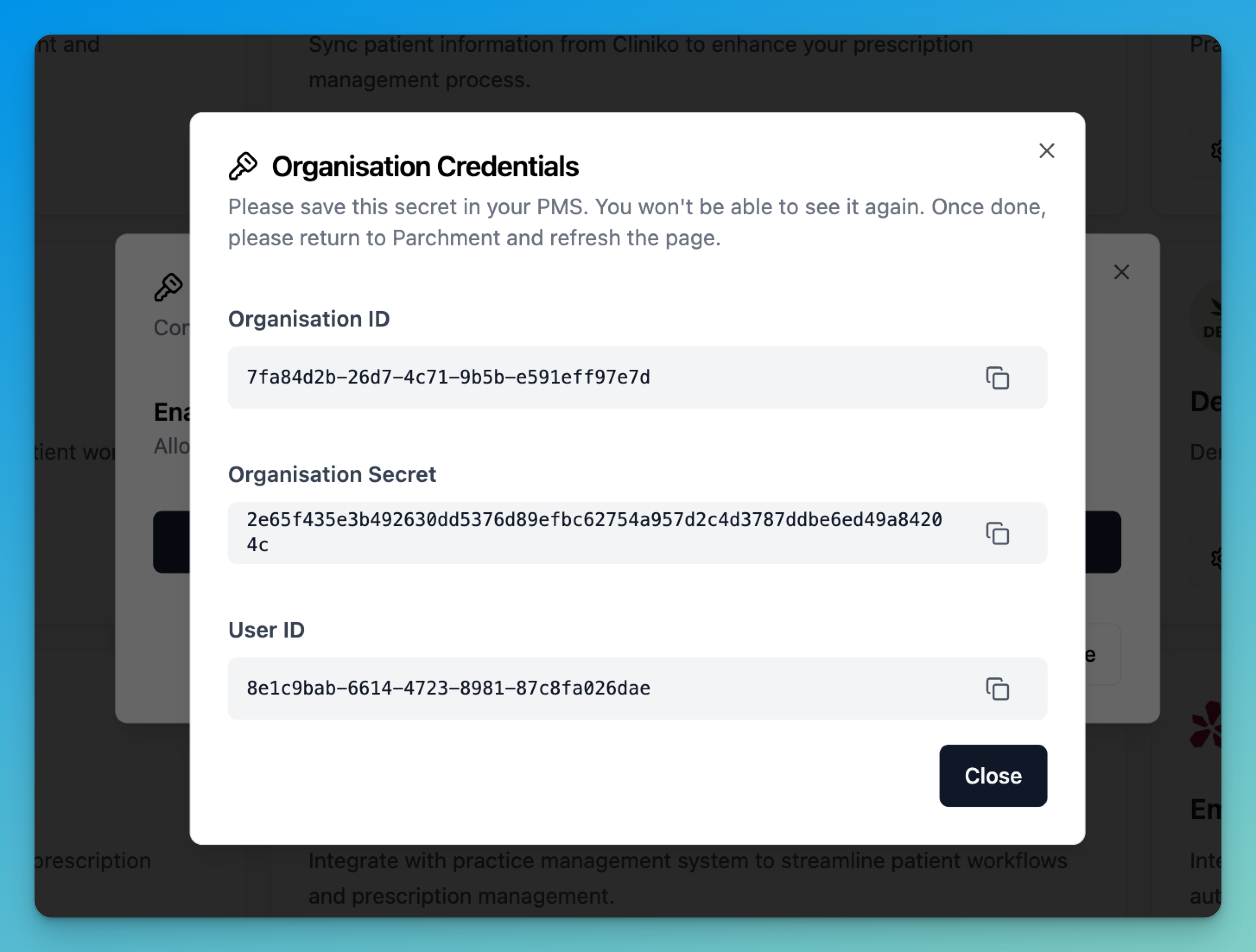
- Copy the partner credentials:
organization_id,organization_secret, anduser_id
Token Request
To generate an access token, make a POST request to/v1/token with the required headers and request body.
Required Headers
| Header | Description |
|---|---|
x-partner-id | Partner ID provided by Parchment |
x-partner-secret | Partner secret provided by Parchment |
x-organization-id | Organization ID provided by Parchment |
x-organization-secret | Organization secret provided by Parchment |
x-user-id | User ID provided by Parchment |
Request Body
| Field | Type | Required | Description |
|---|---|---|---|
grantType | string | Yes | Must be client_credentials |
scope | string[] | Yes | Array of permission scopes to request |

